Security Best Practices for Digital Products: A Non-Negotiable Checklist
Security isn’t a feature you add later.
It’s a baseline expectation users never see—until it fails.
For modern digital products, security incidents don’t just cause downtime. They erode trust, trigger compliance fallout, and create long-term brand damage that’s hard to reverse.
This guide lays out a clear, practical checklist for digital product security. It’s written for product teams, founders, and engineers who want to ship fast without shipping risk.
WorkSub - 30% cost savings vs traditional agencies
Why Digital Product Security Is Non-Negotiable
Security decisions compound over time.
Early shortcuts—hardcoded secrets, weak auth flows, missing audit logs—become structural weaknesses as products scale. Fixing them later is slower, riskier, and more expensive than doing it right upfront.
Strong app security best practices protect:
- User data and privacy
- Business continuity
- Legal and regulatory standing
- Long-term product velocity
Security isn’t about perfection. It’s about reducing blast radius.
Authentication and Access Control Essentials
Authentication is the front door. Access control is what rooms users can enter.
Identity and Authentication
At a minimum, every digital product should have:
- Secure password handling (hashing + salting) or go passwordless
- Multi-factor authentication for sensitive actions
- Rate limiting on login attempts
- Secure session management
Avoid rolling your own auth unless you absolutely have to. The attack surface is larger than it looks.
Authorization and Permissions
Authentication answers who you are. Authorization answers what you can do.
Checklist:
- Role-based access control defined explicitly
- Least-privilege defaults for all users
- Server-side permission checks (not just UI gating)
- Clear separation between admin and user actions
Most breaches involve over-permissioned accounts, not broken passwords.
Data Protection and Privacy by Design
If your product stores data, you are responsible for protecting it—full stop.
Data Encryption
Every modern product should ensure:
- Encryption in transit using HTTPS everywhere
- Encryption at rest for sensitive data
- Secure key management and rotation
- No secrets stored in code repositories
Treat encryption as table stakes, not a differentiator.
Data Minimization and Retention
Security improves when you collect less.
Ask:
- Do we actually need this data?
- How long should we keep it?
- Who can access it internally?
Define retention policies early. Old data is a liability.
Secure Development Practices That Scale
Security doesn’t live in one tool. It lives in your workflow.
Secure Coding Standards
Adopt consistent standards for:
- Input validation and sanitization
- Safe handling of user-generated content
- Protection against common injection attacks
- Defensive error handling
These habits prevent entire classes of vulnerabilities.
Dependency and Supply Chain Security
Third-party libraries are powerful—and risky.
Checklist:
- Track dependencies explicitly
- Monitor for known vulnerabilities
- Remove unused packages
- Pin versions intentionally
Many breaches originate from outdated or abandoned dependencies.
Infrastructure and Deployment Security
Production environments deserve different rules than development.
Environment Separation
At minimum:
- Separate dev, staging, and production
- No shared credentials across environments
- Restricted access to production systems
Accidental access is still access.
Secrets and Configuration Management
Never treat secrets casually.
Best practices include:
- Centralized secrets management
- Environment-based configuration
- Automatic rotation where possible
If secrets leak once, assume they’re compromised forever.
Monitoring, Logging, and Incident Readiness
You can’t secure what you can’t see.
Logging and Audit Trails
Every product should log:
- Authentication events
- Permission changes
- Data access for sensitive records
- System errors and failures
Logs should be tamper-resistant and retained long enough to investigate incidents.
WorkSub - 30% cost savings vs traditional agencies
Incident Response Basics
You don’t need a 50-page playbook—but you do need a plan.
Define:
- Who investigates incidents
- How users are notified
- When systems are taken offline
- How fixes are deployed
Preparation turns chaos into process.
Compliance and Regulatory Readiness
Compliance isn’t optional once you cross certain thresholds.
Understand What Applies to You
Depending on your product and users, you may need to consider:
- Data protection laws
- Industry-specific regulations
- Contractual security obligations
Security and compliance are related but not identical. Compliance sets the floor—not the ceiling.
Document Security Decisions
Clear documentation helps with:
- Audits
- Enterprise sales
- Internal alignment
Write down:
- Security controls in place
- Known risks and mitigations
- Review schedules
This turns security from tribal knowledge into an asset.
Visual Framework: Defense-in-Depth for Digital Products
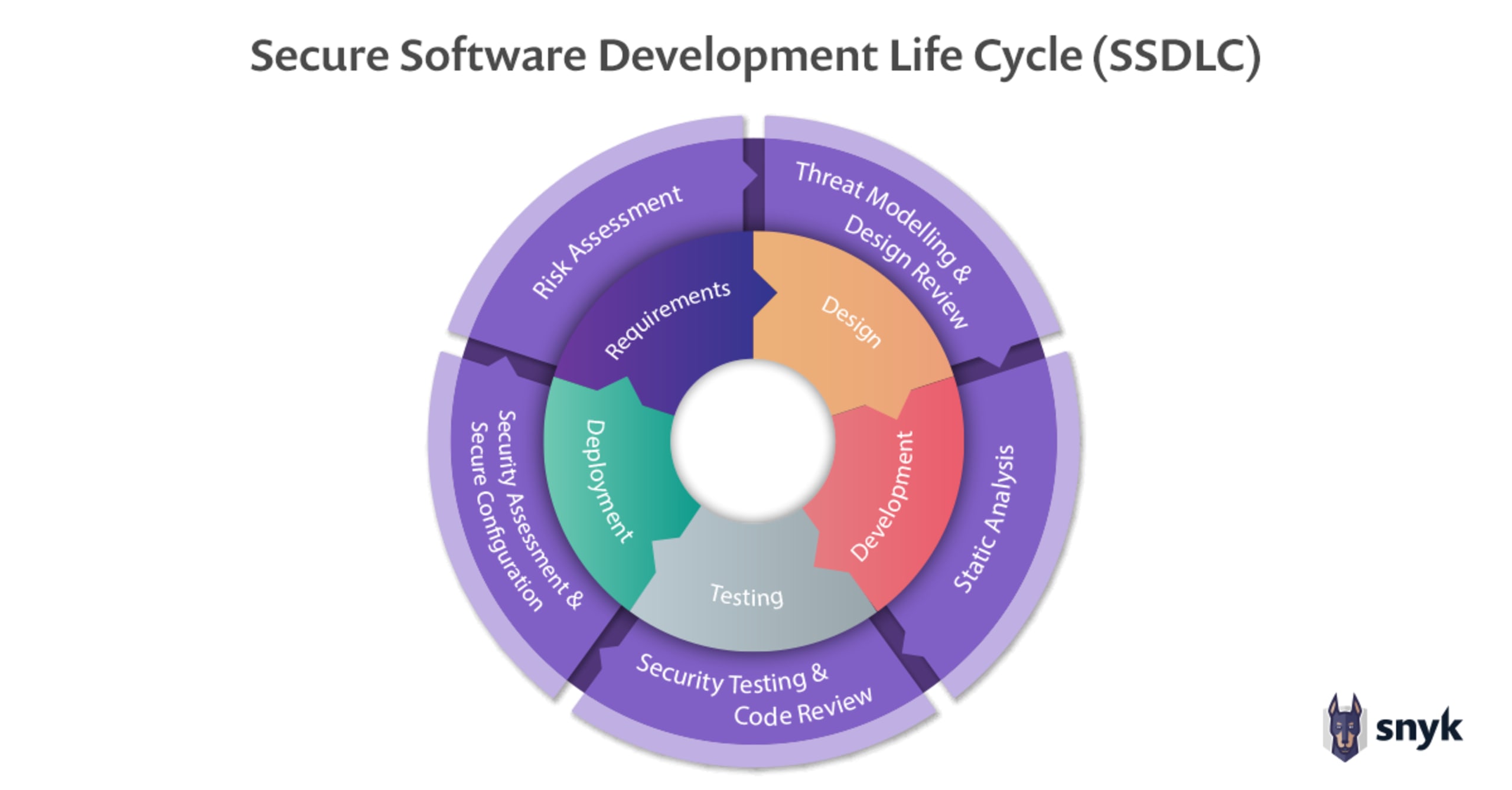

Think in layers:
Identity
→ Access
→ Data
→ Code
→ Infrastructure
→ Monitoring
If one layer fails, another limits damage.
Common Security Mistakes to Avoid
- Treating security as a final checklist item
- Trusting the frontend for access control
- Ignoring internal access risks
- Skipping security reviews for “small” features
- Assuming compliance equals security
Most breaches are preventable with consistent basics.
Plug-and-Play Development Talent for Your Team
FAQs: Digital Product Security
What are the most important app security best practices?
Strong authentication, least-privilege access control, encryption, secure coding standards, and continuous monitoring form the core.
How early should teams think about secure development?
From day one. Early architectural decisions have the biggest security impact.
Is security only an engineering responsibility?
No. Product, design, legal, and operations all influence security outcomes.
Do small startups really need formal security practices?
Yes. Smaller teams have less margin for error and fewer resources to recover from incidents.
How often should security be reviewed?
Continuously for monitoring, and at least quarterly for structured reviews.
Conclusion: Security Is a Product Decision
Security isn’t just about avoiding breaches.
It’s about earning and keeping trust.
Teams that treat digital product security as non-negotiable:
- Move faster with confidence
- Close enterprise deals more easily
- Avoid painful rewrites and public incidents
If you build digital products, security isn’t someone else’s job. It’s part of the product.